You're working on a design project and need to download some images. So, you head over to your favourite stock image site and start browsing. After finding a few you like, you download them and work. You finish the project and send it off to your client a few days later. Everything seems fine...until you get an email from your client informing you that the file you attached is infected with malware after their email system detected some issue in the email you sent earlier. How could this have happened? Unfortunately, malware has become too familiar to hide in design assets and elements downloaded from stock image sites.
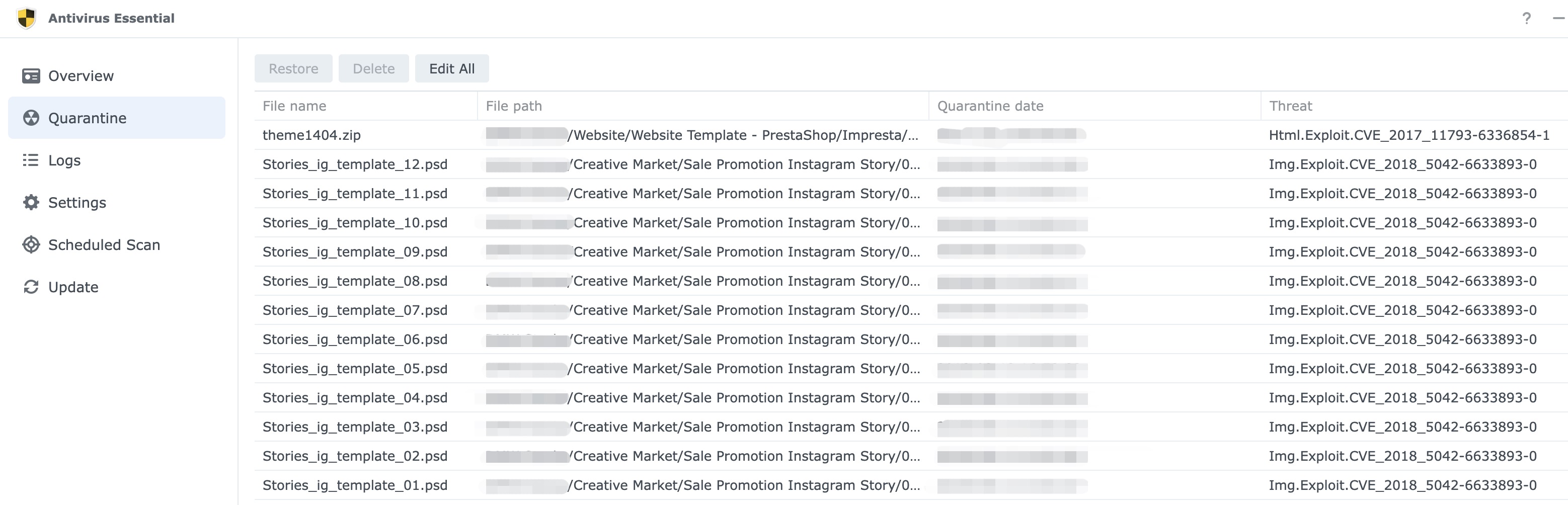
What is Img.Exploit.CVE_2018_5042-6633893-0?
It's a malicious file that exploits a known vulnerability in some software. The vulnerability is identified by the acronym "CVE," which stands for Common Vulnerabilities and Exposures. In this case, the vulnerability is identified as "CVE-2018-5042."
It is important to note that exploitation of vulnerabilities such as this one can allow an attacker to gain unauthorised access to a system or execute arbitrary code. It is essential to keep your software up to date and apply any available security patches to protect against such attacks. If you have this file on your system, you should take steps to remove it and scan your system for any other potentially malicious files.
Where can you find them?
It is difficult to say where a specific malicious file may appear, as attackers can use various techniques to deliver such files to potential victims. However, it is vital to be cautious when downloading files from the internet, especially if you did not intentionally seek out the file or are unsure of the source.
Malicious files can be delivered through email attachments, instant messaging, or by being downloaded from websites. They can also be delivered through software vulnerabilities, such as when a user visits a website that exploits a vulnerability in their web browser.
It is a good idea to be cautious when interacting with unfamiliar files and to run up-to-date antivirus software to protect against known threats. It is also a good idea to keep your operating system and other software up to date, as many vulnerabilities are patched through software updates.
While it may seem safe to download images from a reputable source, the sad reality is that many stock image sites have been compromised by hackers who upload infected files to spread malware. And since designers and other creatives often use these sites, they can be especially vulnerable to attack at any time.
Can a malicious file be payload into an image, pdf or other files?
Yes, a malicious file can be "payload" into an image or PDF file. This can be done by embedding the malicious file within the image or PDF file and then delivering the file to a potential victim.
When the victim opens the image or PDF file, the embedded malicious file is executed, allowing the attacker to potentially gain unauthorised access to the victim's system or execute arbitrary code.
It is essential to be cautious when opening image and PDF files, especially if they were not expected or come from an unfamiliar source. It is a good idea to run up-to-date antivirus software and to be mindful of any suspicious activity on your system.
What is Payload? (For non IT Savvy readers)
In computer security, a payload refers to the part of a piece of malware that performs the malicious action. A payload can be delivered to a victim's system through various means, such as email attachments, instant messaging, or by being downloaded from a website.
Once the payload is delivered and activated, it can perform various malicious actions, such as installing additional malware, stealing sensitive data, or disrupting the regular operation of the system.
The payload is often the essential part of the malware, as it carries out the intended malicious actions. It is essential to be cautious when interacting with unfamiliar files and to run up-to-date antivirus software to protect against known threats.
You can take a few steps to protect yourself and your clients from this growing problem. First, you can just run a virus scan on all files after downloading them and always run a virus scan fortnightly as some virus doesn't surface after unpacking. Smart cybercriminal knows how to make their tools hibernate and hide away, avoiding all kinds of detection. And finally, I would like you to only download images from sources that you trust. Taking these precautions can help ensure that the files you download are safe and free of malware.
Conclusion
The next time you need to download images for a design project, be sure to take extra care to avoid accidentally downloading malware-infected files. Following the tips in this blog post can help keep yourself and your clients safe from infection. Stay safe out there!