You're working on a new design project and need some images to spruce it up. So, you head to your favourite stock image site and start downloading. But you may not realize that those seemingly innocent design assets could hide a dark secret: malware.
That's right, and malware has been showing up in stock image downloads more and more frequently. And while the odds of downloading a malicious image are relatively low, it's still important to be aware of the risks. In this article post, we'll look at how malware is hidden in stock images, why downloaders are such a tempting target for hackers, and what you can do to protect yourself.
How Malware is Hidden in Stock Images
One of the most common ways malware hides in stock images is through steganography. Steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video. So, for example, a hacker could embed malicious code into an image file and then upload that file to a stock image site. When someone downloads the image and opens it, the embedded code would execute and infect their system with malware.
Another way that malware can be hidden in stock images is through mislabeling. This happens when a hacker uploads a malicious file to a stock image site and then gives it a misleading name or description. For example, they might upload a photo that contains ransomware and label it as a "company infographic." If someone downloads the photo without verifying its authenticity first, they could end up inadvertently infecting their system
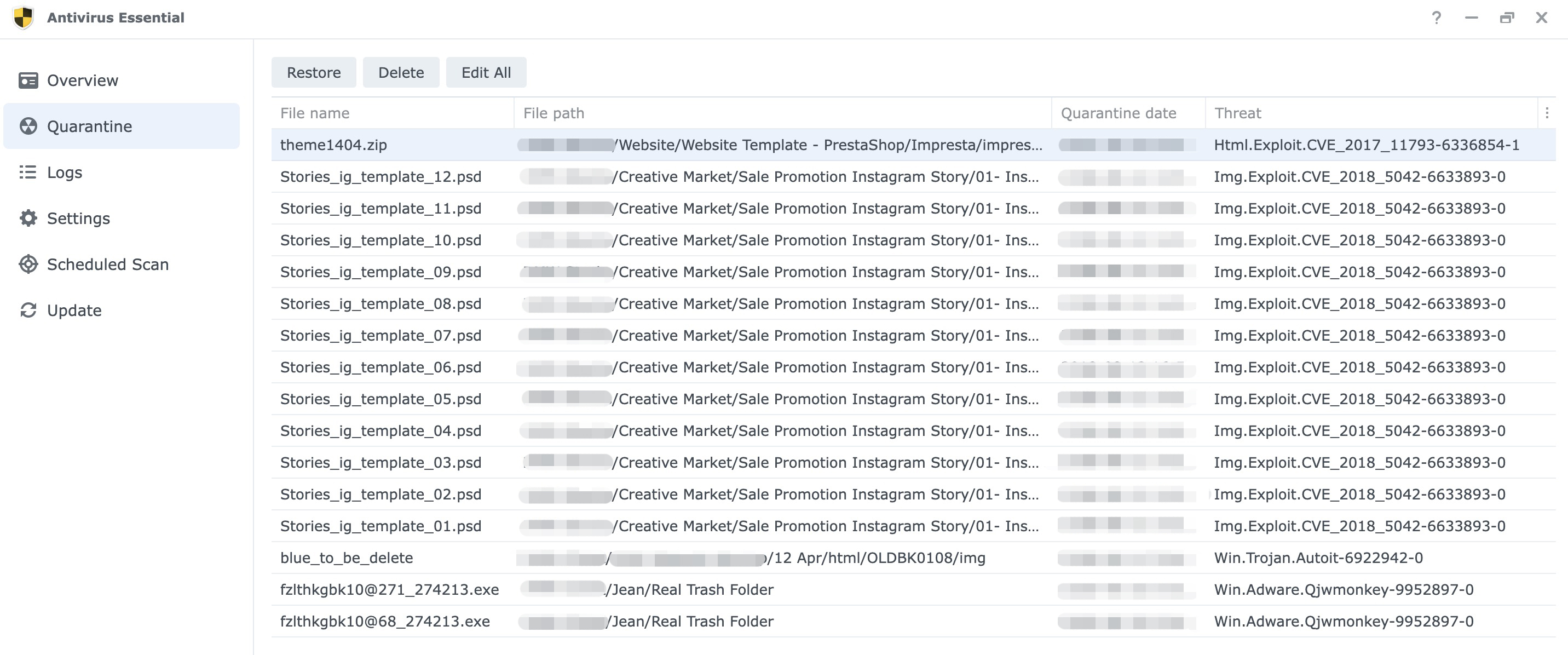
These are malware found in our drive's design assets (theme template for Prestashop, Instagram story design template from Creative Market). Do also look out for employees who bring company assets like laptops and smart devices home that may store hidden malware that may cripple your organisation if there is no prevention.
References:
- Img.Exploit.CVE_2018_5042-6633893-0
"Jack-in-the-Box" Vulnerability When Unpacking Images (CVE-2018-8115) - https://blog.aquasec.com/windows-host-compute-service-shim-remote-code-execution-vulnerability-cve-2018-8115 - Top Docker Security Vulnerabilities, Best Practices, & Insights - https://www.alertlogic.com/blog/top-docker-security-vulnerabilities-best-practices-insights/
- What is a CVE? - Red Hat - https://www.redhat.com/en/topics/security/what-is-cve#:~:text=CVE%2C%20short%20for%20Common%20Vulnerabilities,assigned%20a%20CVE%20ID%20number
- What is a CVE? Common Vulnerabilities and Exposures Explained - https://www.upguard.com/blog/cve
- Win.Trojan.Autoit-6922942-C - https://www.f-secure.com/v-descs/trojan_w32_autoit.shtml
- Adware.Win32.Qjwmonkey.E - https://www.fortiguard.com/encyclopedia/virus/6595115 https://www.trendmicro.com/vinfo/ie/threat-encyclopedia/malware/Adware.Win32.Qjwmonkey.E/
Why Downloaders are Such a Tempting Target for Hackers
Two main reasons downloaders are such attractive targets for hackers are reach and permission. When someone visits a stock image site and starts downloading assets, they're effectively opening up their system to any malicious files lurking among the legitimate ones. And once those files are on their system, they can potentially do serious damage.
Users effectively permit hackers to access their systems by visiting a stock image site and downloading assets from it. Hackers know this, so they often try to hide their malicious code in otherwise innocuous-looking files like images or videos.
How You Can Protect Yourself from Malware-Laden Stock Images
The best way to protect yourself from accidentally downloading malware-laden stock images is to exercise caution when selecting which assets to download. Only download files from reputable sources and pay close attention to the file names and descriptions before downloading anything. Additionally, make sure that your system is protected by antivirus software so that you can catch any malicious files that manage to slip through the cracks.
Conclusion
Stock image sites can be great sources of inspiration and design assets for your next project—but you need to be careful about which ones you use. Many of these sites host thousands (if not millions) of files uploaded by individuals worldwide. Some of them may be hiding malware in otherwise innocuous-looking images. To protect yourself from accidentally downloading a malicious file, only download assets from reputable sources and always pay close attention to file names and descriptions before clicking "download." Additionally, make sure that your system has antivirus protection so that you can catch any malicious files that manage to slip through the cracks.
Avoid employees bringing company assets back home without proper knowledge as they may use them on non-company-related stuff that might cause wanted circumstances to your organisation.
Image from @lazycreekimages : Unsplash